Building an Ethernet Tap
January 19, 2006 at 12:07 AM | categories: electronics, diy | View Comments
Overview
Recently, I've been teaching myself about network protocols and have also written a network sniffer program: ECSniff which exemplifies the importance of using encryption whenever you transfer sensitive information. Well anyway, ever since I wrote the software, I've wanted to play around with it a bit. Problem is, on todays networks, it gets a bit complicated if you want to see anyone's network traffic but your own. I run an SSH server on my DSL line that has been getting several break in attempts recently (usually someone in Italy trying random usernames and passwords), so I would like to build an Intrusion Detection System to alert me if they ever come back and I'd like it to be a seperate computer from the SSH server. To do this, I need to build an Ethernet Tap to get around the security features built into todays modern switched hubs.
History Lesson
Analyzing network traffic is not as easy as it once was. In the old days we used hubs to connect computers together on a LAN. Hubs are really simple devices. Whatever data comes into it, it simply sends it right back out to all the rest of the ports. Since network packets have the destination encoded in them, the computer that the packet is intended for is then supposed to read it, while all the other computers on the LAN, although they too received the packet, are supposed to ignore it. Talk about a trusting relationship! Would you ever send out your credit card information to everyone in the neighborhood with a post-it-note stuck on top that says "don't read this unless you're Bob"? No!
We've gotten a lot smarter about things since then. Today we use switched hubs instead. Switches are devices that subdivide networks into network segments. If you put a switch in between two hubs, then any data transmitted on hub 1 will stay on hub 1 unless it is actually desired to talk to someone on hub 2. A switched hub goes one step further: it puts a switch on every single port of the hub. This means that if you are on port 1 of the switched hub and you want to talk to someone on port 3, then no other port on the device will see that information, just port 3. This is really done for two reasons 1) For speed and 2) For security. On an old hub, all traffic is half-duplex, that is, when one computer is talking, everyone else has to shut up and listen. On a switched hub, traffic is full-duplex. Everyone can whisper to each other at the same time and no one gets confused. As a side benefit, it is more secure (although still very insecure if you still use plain text protocols) because only your intended recipient actually receives the data.
Sniffing a Switched Network
So if all modern networks are switched, how can I sniff data intended for other computers? For this I set out to do a bit of research.
There are actually several ways to do it as long as you have physical access to the network hardware. Today, the most common way is to use a Port Mirror. A Port mirror is an ability that some switches have that allows a single port to act as if it were on a normal hub, that is, it receives the traffic intended for one or many of the other ports. In the business world, Port Mirroring is the most common way to implement an Intrusion Detection System (IDS) on a LAN. Since the switch and router companies realize that businesses want to do this, they build the ability right into their equipment... For a price. I have yet to find a switch that has this ability for less than a couple hundred bucks. Suffice to say, I don't own one.
There is however a simpler, cheaper and actually better solution: an Ethernet Tap. An Ethernet Tap is a device that you plug right into the Ethernet cable. It detects all traffic that flows on it in either direction. Here is a diagram:
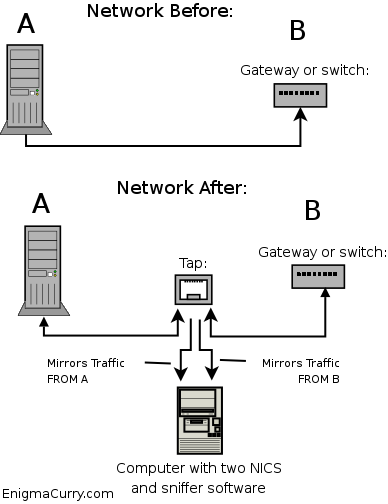
In the above diagram, A is a single computer (or it could be a switch) and B is a switch (or it could just be another computer, it doesn't really matter what these devices are). The Tap splits the connection between A and B. The connection inside the box is unbroken, that is, A is still physically attached to B. However, along the way, the transmit lines of A get mirrored as well as the transmit lines of B. These mirrored data lines are taken to a computer with some sort of sniffing software installed. Using a Tap requires the sniffing computer to have two network cards. One for A's transmissions and one for B's. So as to completely isolate the sniffer computer from the network, the sniffer's transmit lines are not connected. The sniffer computer can only "see" the data but can't "touch" it, effectively making the sniffer computer invisible on the network.
Building an Ethernet Tap
The Ethernet Tap is a passive device, it requires no external power. It's just a bunch of wires in a specific configuration. You can easily make this device yourself for less than 20 US FRN (btw, that's 20 US Federal Reserve Notes, not dollars, I call a spade a spade. Read about weights and measures in the US constitution and you'll understand why.)
I decided to make one myself and here is the parts I acquired from Home Depot:
- 4 category 5e network jacks. I actually bought a box of ten, they were cheaper that way. (3 FRN a piece)
- One four jack face plate (2 FRN)
- One blue electrical box (2 FRN)
- 6 inches of cat 5e cable (I actually just had this lying around)
Total: 16 FRN
The wiring is really quite easy. We have four ports. One that connects to host A, one that connects to host B and two tap ports. One tap port for all of host A's transmissions and one tap port for all of host B's transmissions. You wire host A to host B straight through pin for pin the same. Then just continue the transmission lines for each host down to the tap port for that host.
Here's a diagram (The dotted lines are the sriped wires, the sold colored lines are the solid colored wires):
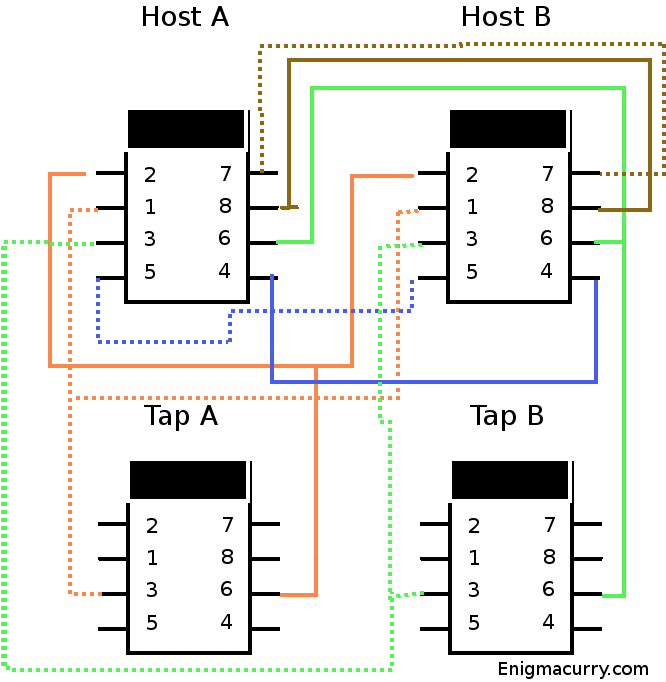
Strip the cat 5 cable and untwist all the individual wires. Place a jack in the upper left spot (from the front) in the faceplate. This is the Host A jack. Punch down all the wires for this jack with the little punch tool that came with it.
If you do one jack at a time it's easier:

Next put in a jack in the spot directly below it. This is the Tap A jack. Lace the orange wires from the host A jack to this jack and punch them down. You should still have several inches of the orange wires hanging off at this point. Now put in the host B jack to the right of host A. Lace all the wires except for the green ones (this includes the orange ones from Tap A) and punch them into the host B jack. Now without putting the tap B jack in the faceplate lace the green wires to it and punch them down, then lace the remaining length of green wires to the host B jack and punch them down there as well. Now put the tap B jack onto the faceplate.

At this point all of the wiring is done. You can now test to make sure it works. To protect the wiring, I wanted to put it in some kind of a box. I wasn't able to find a very good solution at Home Depot. What I did find though, was a blue electrical box that the faceplate would screw on to. It is MUCH larger than it needs to be, but it's not too bad looking (I'll probably look for a better box, or craft one of my own):

And there you have it, you're very own Ethernet tap.
ECSniff 0.6 released
January 17, 2006 at 11:56 PM | categories: python, security | View CommentsI've just made an update to the Enigma Curry Network Sniffer.
Version 0.6 includes the following changes:
- MSN instant message logging
- FTP authentication logging
- HTTP web page access logging
- Subnet Filtering
Google Talk now (fully) supports Jabber!
January 17, 2006 at 09:45 PM | categories: uncategorized | View CommentsI've been highly critical of Google ever since Google Talk came out. Google Talk is based upon the open-source, patent free, instant messaging protocol called XMPP otherwise known as Jabber. Unfortunately, Google Talk has never been able to talk to other Jabber servers. That is, until today.
Today, Google flipped the switch that allows all Google Talk users to talk to all Jabber users.
Why is this such a huge deal? Think back to the days before the internet got big, when email was just starting to become popular. There were several providers to choose from. However, if I was on Compuserve and you were on Prodigy, we couldn't (easily) email each other. Worse yet, if I wanted to start my own little internet service provider, there was absolutely no way my customers could email you. Then along came the idea that email could use DNS. Letting DNS tell email servers how to route emails was revolutionary. Anyone could email anyone, anywhere, no matter what service provider they used. The Instant Messaging industry is in the exact same situation as email was before it used DNS. If I'm on MSN, I can't instant message you on Yahoo. Jabber, on the other hand, is an open protocol that uses DNS to route messages just like DNS routes email. I can have my own jabber server running on enigmacurry.com and I can instant message you on your server running on yourcoolserver.com.
However, Jabber has not gotten very big because no big company (like MSN, Yahoo and the like) have any incentive to dethrown themselves off the IM food chain.. and because all the IM services are free anyway and there is such a huge user base already, the users have little incentive to change either.
Today, Google fully embraces Jabber. This means that Jabber now has a huge company with large amounts of dollars publicly declaring that you can use whatever network you want (that uses Jabber) and connect to us and talk with our users. The incentive that Google has though, is that they will be first. If Google plays it right, pushing the "openness" of it all.. people will flock to it.
Good move Google.
Now, I'm off to make some "additions" to ECsniff.. You can pry gaim-encryption from my cold dead DSL line.
ECSniff - Introducing the Enigma Curry Network Sniffer
January 13, 2006 at 01:59 AM | categories: python, security | View CommentsI was talking to my friend Gandhi today. He's taking a really lame computer networking class this semester in order to fulfill graduation requirements. He's confident that he won't be learning a thing in the class.
This worries me a bit. I was told by one of my professors a few years ago that I would not need to take this class. Now Gandhi is being forced into it. Despite my having several years of experience in the field already, soon, I too may be forced into answering questions like "What is an IP address?" or even worse "How does the Internet make our lives easier?"....... shudder and shudder.
Maybe I can prove to them that I really don't need to take the class. I thought of showing them a picture of the server room at work. We have a little under 70 computers in there. All networked and maintained by me. Then again, maybe they think the class will teach me "the deep internals of networking" or something equally untrue of the class. So, I thought if push comes to shove, I'd show them that I can find anyone's email password on the network (assuming I have physical access of course)
So without further ado, here is the Enigma Curry Network Sniffer.
This software is by no means original. There are umpteen different other programs out there that will do similar things. I wrote this one, however, by only reading the RFC documents available on the various protocols used. I wanted to make sure that I knew much more than will ever be taught in this dumb IS course. Plus, it was pretty fun to write.
Right now this software only does two things. It will scan the local network for connections to POP3 email servers and HTTP servers using Basic Authentication. Anytime someone on the network uses one of these very insecure protocols, it will display their username and password on the screen of the person running this program. You can also leave the program running and log the results to a file. For future versions, I think it would be fun to explore some instant messaging protocols like MSN... it would be fun to prove the necessity to some of my friends and coworkers of using Gaim-Encryption.
Go download the software if you'd like to try it out, but please don't get yourself into trouble! I take no responsibility for your actions.
ECSniff: The EnigmaCurry Network Sniffer
January 13, 2006 at 12:07 AM | categories: python, software | View CommentsContents
OverviewFeatures
Requirements
Command line options
Example Usage
FAQ
Revision History
Overview:
This is my take on a network sniffer. It allows you to see interesting data that is on your network. Not just the data that is intended for your computer but for other computers on the same LAN as well. So far, this has only been tested on Gentoo Linux x86_64, but should work on any platform that supports Python as well as libpcap (Most Linux distros already have this installed) or Winpcap (for windows).
This software is intended for educational purposes. Nevertheless, usage is granted to anyone under the terms of the GNU General Public Licence version 2. What you do with it, as well as the consequences of using it, is your own responsibility.
Features:
Version 0.6 has the following features:
- Log HTTP web page accessess
- Log HTTP authentication attempts (username and password)
- Log MSN instant messages
- Log POP3 email authentication attempts (username and password)
- Log FTP authentication attempts (username and password)
- Subnet filtering -- This allows you to stay out of trouble by only logging some computers
- Write all log info to a file for later analysis
Requirements:
- Python 2.4 (haven't tested older versions)
- Pylibpcap
- Libpcap or Winpcap
Download:
ECSniff.0.6.tar.gz- version 0.6 released Jan 18 2006- Moved over to github -- Note, I'm not working on this project any longer. This is more of a code dump than anything else.
Command line options
options:
--version show program's version number and exit
-h, --help show this help message and exit
--subnet=IP/netmask Only display data for a specific subnet. eg:
192.168.0.1/24 or 192.168.0.1/255.255.255.0
--pop3 Log POP3 usernames and passwords
--httpauth Log HTTP usernames and passwords
--http Log HTTP/WWW page accesses
--msn Log MSN messenger messages
--ftp Log FTP usernames and passwords
-e, --everything Log Everything
-d device, --device=device
device to sniff (eth0, wlan0 etc)
-l file, --log=file log results to file
-q, --quiet don't display events on stdout
Example Usage:
These examples assume you are running Linux. Linux requires you to have root access in order to log data from the network device. So do the following commands as root or with the sudo command. In these examples, wlan0 is my network device. Change the devicename to whatever device you want to examine (eth0 is usual).
Log all POP3 email connections:
./ecsniff.py -d wlan0 --pop3
Log all HTTP web page accesses and also log HTTP Basic Authentication attempts:
./ecsniff.py -d wlan0 --http --httpauth
Log all MSN messages making sure to only log messages in and out of a particular machine with a local IP address of 192.168.1.50:
./ecsniff.py -d wlan0 --msn --subnet=192.168.1.50/32
Subnet filtering is a very important feature. It can be illegal for you to log network traffic of computers that you are not the legal user of. By default, ecsniff will log all packets regardless of their source or destination. By specifying a subnet, you can limit which IP addresses are logged. With subnet filter turned on, all packets that are logged will either be from the specified subnet or be destined to that subnet.
Log Everything (that ecsniff is desinged for) from the local lan (subnet 192.168.0.0 netmask 255.255.255.0)
./ecsniff.py -d wlan0 --everything --subnet=192.168.0.0/255.255.255.0
You can specify the subnet using either the full netmask (255.255.255.0) or by it's shorthand (like in the example before)
If you are unfamiliar with netmask shorthand see this page
FAQ
Is this a hacker tool and is it illegal?
The purpose of this program is to be a DEMONSTRATION that we still use some pretty insecure protocols these days. It is is probably useful to the script-kiddie as well, but that is not my intention. In some countries it is illegal to eavesdrop on communication that is not your own. So don't go eavesdropping on other people's business!
I don't want to break the law, how can I just look at MY network traffic?
If you want to stay out of trouble, use the --subnet option. For instance if your local IP address is 192.168.0.2 and you only want to log your own traffic use the option "--subnet=192.168.0.2/32". You won't see any one else's traffic but your own.
How can I avoid being a victim of this or similar programs?
Use encryption! Don't use any network protocol that sends information in plain-text for transmitting information that you think is important. For email, use the GNU Privacy Guard with SSL for authentication. For instant messaging, use Gaim with Gaim-Encryption (works on all networks, MSN, Yahoo, AIM etc). For Websites that ask for a password, always make sure that SSL is enabled, if you don't see the lock icon, don't use that website... and never, ever, use Telnet.
I am trying to see traffic on my LAN, but I can't see any other traffic but my own.
In order to be able to see other computer's traffic you have to physically be on the same network segment. Traditionally, when you network computers together using a hub, every computer hooked into that hub (or secondary hubs that are plugged into it) are all on the same segment. Today, more often than not, we use switches not hubs. A switched network uses a unique network segment for each port on the switch. This is done for two reasons: 1) The network is faster if data only has to travel to the intended recipient and 2) People realized that hubs were a major security risk in that anyone could sniff out other people's data (as this program shows).
Even if you are on a switched network, however, you can still sniff the data from all computers if you have physical access to the network equipment. You can use a switch that has a 'port mirror'. A switch that has such a feature will allow you to replicate all traffic on one port (or on a good switch, from all ports) to any other port. In this sense the switch acts like a hub, but only on one specific port (the port you'll use for the sniffing).
Another option, if your switch doesn't support port mirroring, is an ethernet tap. An ethernet tap is something you plug in line with your gateway. All traffic goes through normally, but it also allows you to sniff data right off the line. Here are some instructions for building one very inexpensively. The real nice thing about this particular network tap is that it is completely passive; the transmit lines on the sniffer computer don't go anywhere, so the sniffer computer just "sees" the data that is on the line and cannot "touch" the data or add new data. So, with a tap, no one will find your sniffer, that is, unless they physically find the tap.
One caveat about a tap is that it seperates the full duplex communication into two half duplex signals on two ports. So you have one port having everything sent by Computer A and the second port everything from Computer B. If you want to analyze both Receving and Transmitting on one interface (which currently this program requires) you need to consolidate the two signals back into one. You can use a switch that has port spanning capabilities to do this.
See the Ethereal Capture Setup page for more setups that allow packet capture on switched networks.
Revision history:
- 0.6 - Jan 18, 2006 - Now includes MSN messenger logging, HTTP web page access logging, FTP authentication logging, and Subnet filtering. Licencing information is more explicit. Things are more organized in seperate .py files.
- 0.5 - Jan 13, 2006 - Initial Release. Can scan for pop3 email username and password as well as HTTP Basic Authentications.
Next Page »
